Information security policy
Information security policy
This section provides information security policy for Agora services.
Agora services provide built-in encryption and customized encryption. You can use either of them to implement encryption. The following diagram describes the encrypted data transmission process:
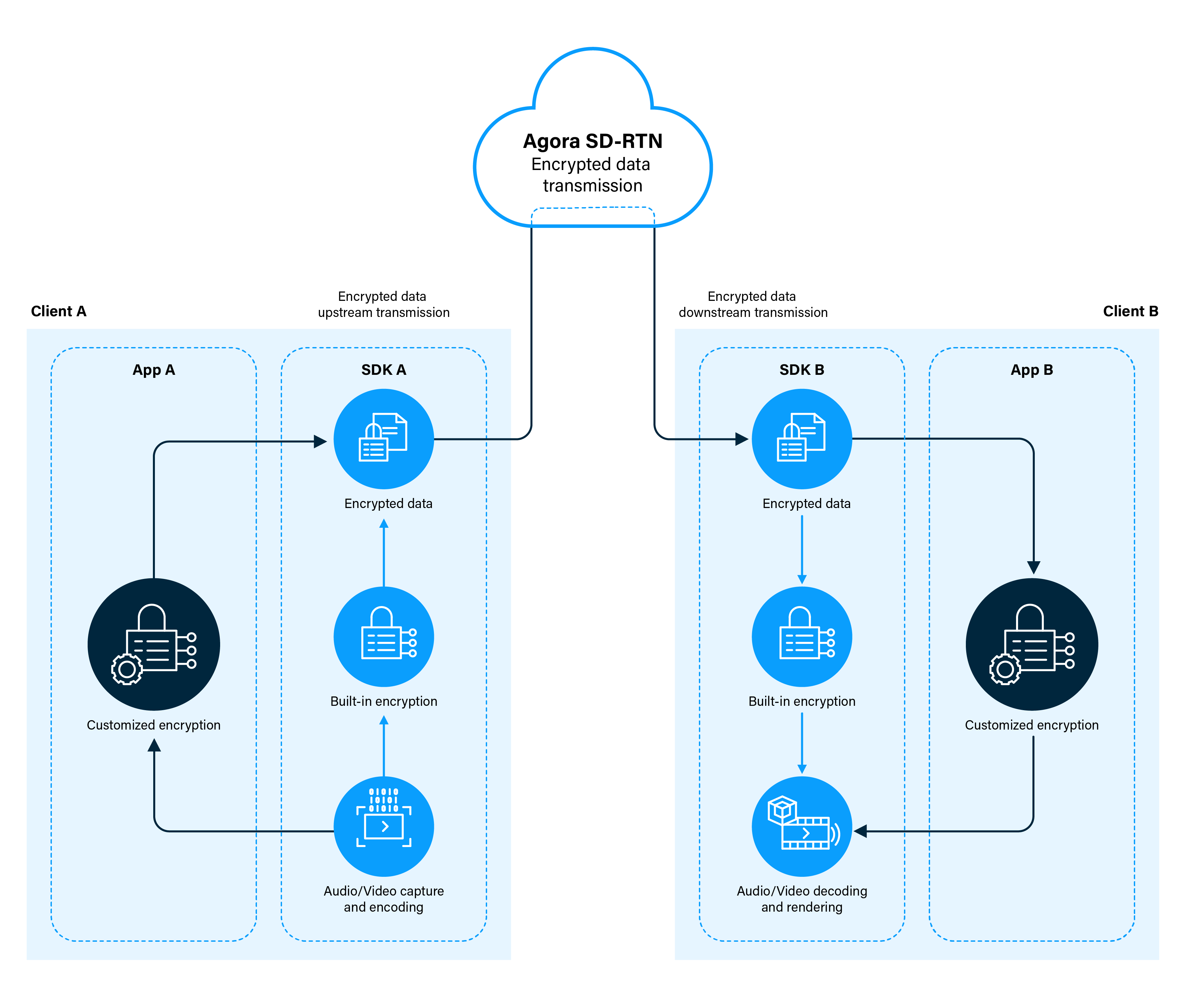
Purpose
Agora is committed to safeguarding the confidentiality, integrity, and availability of all users' physical and electronic information assets.
- Confidentiality against unauthorized access and eavesdropping
- Integrity against tampering and forgery
- Availability of data transmission through the Agora SD-RTN™
Scope
This article describes how Agora protects customer data with security controls.
Data classification
All customer data, in all formats or media types, is classified according to the following categories and protected accordingly.
| Category | Description |
|---|---|
| Customer Account Data | Information related to the customers' Agora accounts, including customer ID, customer IP, network type, operating system, email address, telephone, product interest, programing platform, UTM information, identity, company name, company URL, billing information, trade information, purchased package information, project status, ticket, member information and console access record. |
| End User Data | Information collected by customers related to end users' personal devices and network, including microphone and camera information, CPU status, memory status, battery status, system version, phone model, phone signal level, received signal strength indicator (RSSI), network type, user attributes and channel attributes. |
| Call Content | Audio and video data of the user during a call. |
| Log | Media server logs generated by the Agora servers when accessing the Agora SD-RTN™. |
Data security
The communication between the user and the Agora server is protected by transmission protocols, such as the Agora private transmission protocol, Transport Layer Security (TLS) and Web Socket Secure (WSS). You can also use Advanced Encryption Standard (AES) or a customized encryption algorithm for the encryption of audio and video data.
During data transmission, the Agora SD-RTN™ does not transmit any encryption key information. Call content information can only be decrypted on the terminal device (such as the client app and the customer's on-premise recording server) through the client authorization key.
Data availability
- Large and distributed data centers: Agora has multiple data centers providing services globally, and any attack on one data center cannot affect others.
- Rapid recovery: When a data center is subjected to malicious attacks that are difficult to prevent, such as a distributed denial-of-service (DDoS) attack, Agora will automatically isolate the data center and avoid affecting users' services.
- DDoS attack prevention: Agora has deployed anti-DDoS firewalls in each core cloud data center. Agora has more than two hundred distributed data centers around the world, which guarantees sufficient capabilities and resources to control the risk of DDoS attacks.
Data storage
Agora provides customers with the Agora On-Premise Recording SDK and Agora Cloud Recording, enabling customers to record part or all of the call contents. When using the recording services, all recorded video or audio files are stored on the storage server provided by the customer.
Access authorization
End users can access the Agora SD-RTN™ using a dynamic key, see Set up Authentication.
Electronic access controls
Agora strictly controls the data access on all internal systems. All users have independent internal accounts and authorization systems, and must pass two-step verification. All access records are recorded.
All servers involving user data are strictly audited and protected. Agora employees will only access the production server when necessary, and only by obtaining temporary authorization. Operation records are kept for the whole process.
Physical access controls
All operating servers are hosted in computer rooms that meet ISO 27001 or above information security management certification standards, and all computer rooms protect information security in accordance with the escrow agreement or the Data Protection Association (DPA). Both third-party hosting providers and Agora employees must be approved before they can access servers and equipment.
Roles and responsibilities
Agora sets the responsibilities for its own staff and customers. See the following sections for more information.
Roles and responsibilities within Agora
Security roles and responsibilities within Agora are categorized as follows:
| Role | Responsibilities |
|---|---|
| Information Security Sub-Committee | The Information Security Sub-committee (ISSC) is responsible for the development and implementation of policies and procedures. The ISSC monitors company adherence, and conducts regular technical and non-technical evaluations of Agora security policies. The ISSC also designates which employees are authorized employees. |
| Authorized Employee | An authorized employee has access to the production machines required for the support and maintenance of the Agora service as determined by the ISSC. |
| All Other Staffs | All other staff are required to maintain confidentiality as required by their terms of employment and are required to immediately report of any security breach. |
Shared responsibilities
When evaluating the Agora SD-RTN™, it is important for customers to understand and distinguish the following security measures:
- The security measures that Agora implements and operates.
- The security measures that customers implement and operate to ensure the security of call content information and application when using the Agora SD-RTN™ services.
Customers retain control of the security measures they choose to protect their personal information, platform, applications, systems, and networks. Agora customers should be responsible for all information they collect from users and themselves, such as application logins, identities, passwords, payment information, names, and addresses.
Agora recommends adding obvious prompts before accessing the users' personal information. For example, add an Enable/Disable button with which the user can agree or disagree to share personal information.
Security training
Agora conducts information protection, security and compliance training for all new employees. Agora also ensures that all employees receive information confidentiality training at least once a year. All authorized employees (employees who have access to the production machines) will receive additional training.
Non-compliance
Employees must comply with confidentiality agreements and internal security systems. If a non-compliant situation occurs, Agora will take the corresponding measures depending on the severity of the situation, including but not limited to having conversations with the at-fault employees, strengthening training and education, dissolving labor agreements, and pursuing other legal liabilities.
Reporting potential security risks
Please report any potential risks of Agora services that you may notice to security@agora.io. Please use our PGP public key (Key ID: 2F4553BE) to encrypt your report, as potential security risks are usually sensitive. We assure our security experts will handle the issue immediately once they receive your report.
To facilitate troubleshooting and verification, please include the following information in your email:
- Your contact information.
- The version of the impacted SDK or solution.
- Description of the potential risks.
- Miscellaneous technical details, such as your system configurations, methods or steps for reproducing the issue.
To better protect our system and customers, Agora also invites security researchers to report any bug or vulnerabilities they discover to us. Click Bug Bounty to know more.
Security FAQ
How do I use an Agora SDK to protect my data security?
To ensure the security of the transmitted data, Agora services provide the encryption for audio and video data. Customers can use AES-128/AES-256 or other algorithms preset by Agora, or use customized encryption algorithms to achieve encryption, see Channel Encryption. The encryption key is completely generated and distributed by the customer. Agora recommends that customers use separate keys for each channel to achieve the highest level of data security.
Is Agora AES encryption modes secure?
For network protocol encryption, Agora SDKs use AES_128 mode to encrypt network payload.
For channel encryption, Agora SDKs support AES_128/AES_256 mode to encrypt audio and video. For those who have higher requirements for content security, Agora recommends using our customized encryption. Note that the On-Premise Recording SDK and Cloud Recording does not support customized encryption. For details, please send email to support@agora.io.
Is Agora HIPAA compliant?
Yes.
How does the Agora network respond to DDoS attacks?
Agora regularly scans core network nodes to check and clear possible security holes. Agora also configures anti-DDoS firewalls in each core cloud data center to protect them from attacks. Agora has more than two hundred distributed data centers around the world, which guarantees sufficient capabilities and resources to control the risk of DDoS attacks.
Does the Agora server cache audio and video data?
When using Agora services, the audio and video data are transmitted through the Agora servers. Agora servers cache the audio and video data for 10 seconds during the transmission and release all audio and video data immediately after the call.